An attack initially targeted to hit Spamhaus, an organization that maintains a list of spammers to filter to block the many junk e-mail that everyone receive with great annoyance, escalated in recent days and turned into a real online battle that slowed Internet in various parts of the world.
On March 18, Spamhaus suffered a first DDoS attack after adding the Dutch hosting provider Cyberbunker to its blacklist. Spamhaus turned to CloudFlare, a company that provides various web services, including those connected to security, to set up a defense.
After CloudFlare’s intervention, the attack, which initially generated a traffic around 10 Gbps, has become heavier and heavier. There are techniques suitable to disperse the data packets that arrive during a DDoS attack but when the traffic generated reaches certain levels it’s inevitable that various sections of the Internet get saturated.
In this case, the structures of CloudFlare have also become a target of the attack and the amount of data generated to attack them grew up more and more to reach 300 Gbps. In the largest DDoS attack saw in the past, in 2010, traffic reached about 100 Gbps therefore this latest one is a really an exceptional case.
The delays and the inability to access certain sites are luckily limited mainly to certain areas of Europe but they showed more than ever that the Internet can be vulnerable. This case has shown in particular a certain kind of vulnerability of some DNS servers, which are the ones that turn the websites addresses entered in the browser in the form of URLs into their corrispondent IP addresses.
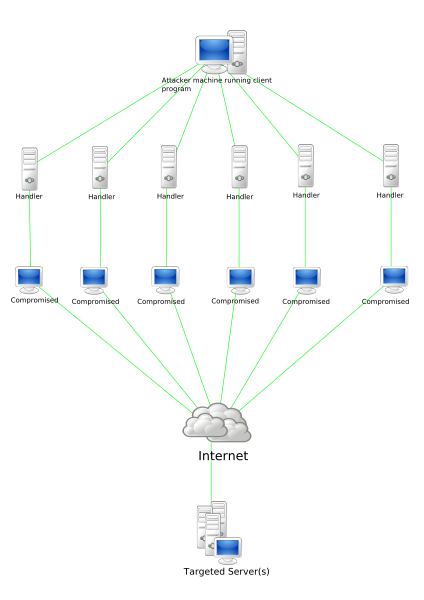
This attack has used a technique called “DNS reflection”, which consists in sending requests to servers with a fake source address so that the response arrives to the target to be hit, in this case Spamhaus and subsequently also CloudFlare. Only some servers are configured to verify the origin of the requests or anyway limit in some way abuses of that kind therefore a well-organized attack can have devastating effects.
This story is far from over and inevitably specialists of various police forces of various nations went into action to investigate. The problem is still the safety of the DNS server, which is linked to that of the users. The computers infected by some malware are turned into zombies: apparently everything works fine but the computer can be controlled by criminals to be used as weapons in DDoS attacks. Servers can be infected too and usually they have a lot of bandwidth available to be used as big weapons in an attack. It’s therefore essential to check that your computers are not infected.
[ad name=”Google Adsense 300″]


Permalink